
In the fog of a Wеb3 security crisis, every incident feels like unprecedented chaos. The ground shifts, trust wavers, and the path forward is obscured.
But beneath the surface of each unique event, a playbook is being written in real-time; a set of guiding principles that separate the projects that endure from those that collapse.
An analysis of two recent, high-profile exploits; one at the social platform UXLink and another at the launchpad Seedify, reveals the two core chapters of this essential playbook: the non-negotiable principles of prevention and the character-defining art of the response.
In Brief:
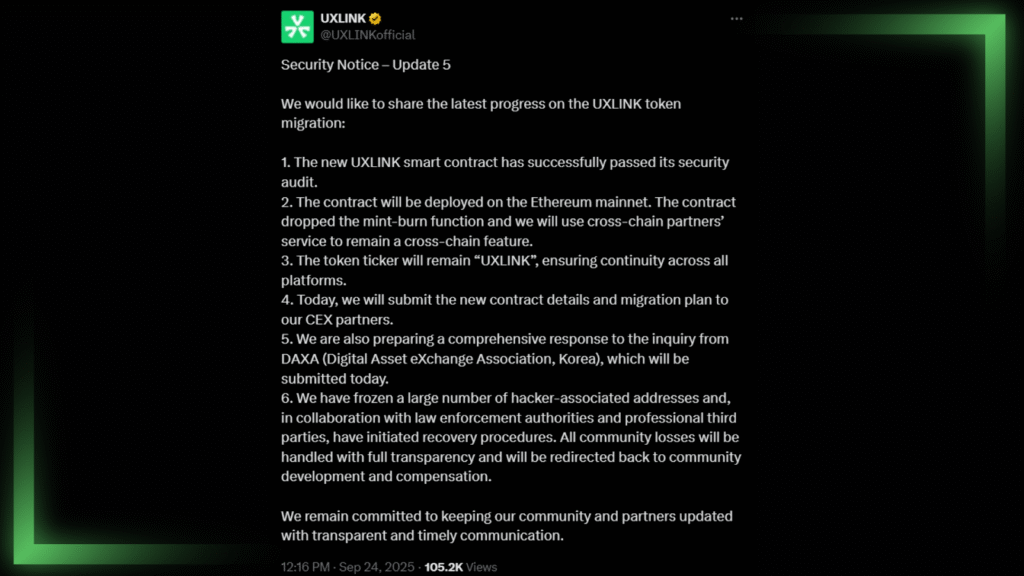
On September 22, the decentralized social platform UXLink suffered a catastrophic breach. Attackers exploited a “delegate call vulnerability” in its multisignature wallet to seize administrative control, minting billions of unauthorized tokens.
The resulting price collapse of up to 90% erased an estimated $70 million in market capitalization and led to direct losses between $11 million and $30 million.
Related: The Hardest Reset: One Developer’s War To Save Shib
In a security analysis, Marwan Hachem, CEO of the firm FearsOff, emphasized the lesson: “Keeping too much centralized control in projects that claim to be decentralized is extremely risky.” He stressed that standard safeguards like timelocks, hard-coded supply caps, and comprehensive audits of the entire multisig setup could have averted the disaster.
But even robust defenses can fail. On September 23, the launchpad Seedify fell victim to a sophisticated, state-affiliated attack.
A single developer’s private key was compromised, allowing unauthorized minting of SFUND tokens via a cross-chain bridge that had, crucially, “previously passed audit.” The hack triggered a 42% token price drop, impacting roughly 64,000 holders and resulting in $1.2 million in stolen assets.
Related: Shiba Inu New Institutional, Global Frameworks Path in 2025
Seedify’s response was a masterclass in crisis management, built on three core actions:
The incidents at UXLink and Seedify, though rooted in security, offer lessons that transcend code. While the specifics of every recovery plan will always be unique to the project and the nature of the attack, the guiding principles for navigating the fog remain universal.
The path forward is paved with a dual commitment: first, to implement the robust, multi-layered preventative measures that honor a community’s trust, and second, to respond to the inevitable storm with radical transparency and a methodical plan. For any community navigating the fog, these principles are not a checklist for criticism, but a compass for shared understanding.
The ultimate measure of resilience is not whether a breach happens, but how teams and communities choose to navigate the path to recovery, together.

Yona brings a decade of experience covering gaming, tech, and blockchain news. As one of the few women in crypto journalism, her mission is to demystify complex technical subjects for a wider audience. Her work blends professional insight with engaging narratives, aiming to educate and entertain.
You cannot copy content of this page